Managed IT Services Onboarding
Easy IT Onboarding for a Smooth Start with Managed IT Support Services, Keeping Your Business Running Securely from Day One
Dark Web Monitoring Service
Our Dark Web Monitoring Service helps protect your business from data breaches due to compromised employee credentials by monitoring the Dark Web in real time and automatically alerting you when it’s time to change passwords because your credentials are up for sale on the Dark Web. Dark Web Monitoring is a must have in cybersecurity protection for businesses.
Within 72 hours, an automated email will be sent to the email address provided to your Sales Rep. This email will come from Dark Web ID <[email protected]>.
The email will contain instructions for logging into your Dark Web Monitoring Account. Here you will be able to view items such as: your Dashboard, Compromises and Reporting.
The email will look similar to the below screenshot:
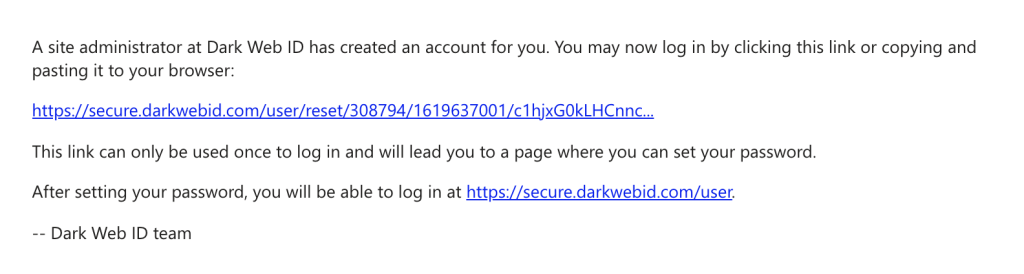
You will be notified via email if and when your data has been compromised on the Dark Web. Here is an example of what the email will look like:
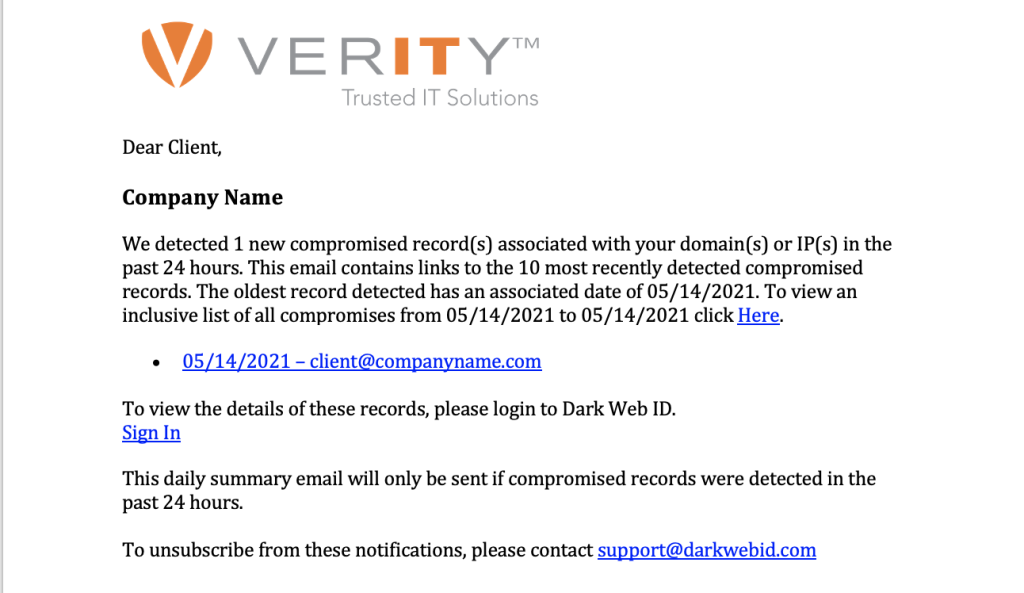
You will receive a “clean bill of health email” if no compromises are found.
It is the client’s responsibility to view and remediate any findings within the Dark Web Portal. Remember, we are monitoring for 3rd party breaches containing your information. If the password contained in the report is indeed yours, remediation is often as simple as changing your password.
Our service is designed to help businesses like yours detect and mitigate cyber threats that leverage stolen email addresses and passwords. We leverage a combination of human and artificial intelligence that scours botnets, criminal chat rooms, blogs, websites and bulletin boards, peer to peer networks, forums, private networks and other black-market sites 24/7, 365 days a year to identify stolen credentials and other personally identifiable information (PII).
The “Dashboard” tab or Cyber Threat Overview provides a graphical representation of your business’s compromises. This will be the first screen you encounter.
Two infographic types will be displayed depending on whether compromise(s) have been detected. If Domains, IPs, and/or emails have been monitored and no compromises have been reported, a blue checkmark will be displayed. If there has been at least one detected compromise, a pie chart will be displayed.
No reports will be sent, as you will have direct access to the Dark Web Monitoring Portal, where you can access your account activity in real time.
You will receive an email daily if and when one of your credentials is compromised on the Dark Web. Otherwise, you will receive a “clean bill of health” email on a monthly basis.
Security Awareness Training
90% of security breaches are inadvertent, unintentional and caused by human error. Security Awareness Training empowers your employees with the knowledge and skills to stay cybersecure at work and at home. With hundreds of awareness and training resources and phishing simulations, you’ll have everything you need to prepare employees to detect, report and defeat cybercrime.
Congratulations on making the choice to protect your business with Security Awareness Training!
In order to get started, please complete and return the Learner List Template to [email protected]. When your completed template is received, we will begin to build out your 12-Month Security Awareness Training Program!
Yes. You will receive an email from your Verity IT Sales Account Executive prompting you to complete a template of learners. Once this is completed and sent back, someone from your company will need to make sure to whitelist sending IPs, domains and header information for phishing simulator.
Verity IT will upload all your learners, schedule the training and phishing simulations and will provide quarterly reports.
Verity IT will provide reports on a quarterly basis.
Explore our Managed IT Services
We provide exceptional managed IT services with a US-based service desk staffed by our own skilled engineers. We offer both remote support and on-site visits when necessary, ensuring comprehensive and effective solutions for all your IT needs and devices.
Our services involve the proactive monitoring, maintenance, and optimization of your IT infrastructure. This includes updating software, applying security patches, managing backups, and ensuring overall system performance and security.
Our Cybersecurity services include firewall management, endpoint protection, email security, security audits, and more. By implementing robust cybersecurity measures, we help safeguard your data and minimize the risk of cyber attacks.
Our Network Monitoring & Management services include monitoring network performance, managing bandwidth, ensuring security, and performing routine maintenance. These services help maintain optimal network functionality, enhance security, and ensure reliable connectivity for your business.
Our services include regular data backups and developing a robust recovery plan to protect your business from data loss due to hardware failures, cyberattacks, or natural disasters. These services ensure your data can be quickly restored, minimizing downtime and maintaining business continuity.
Evaluating, purchasing, and installing IT hardware and software can be time-consuming. At Verity IT, we have the expertise to help you determine the right licensing agreements and hardware for your business. We manage the entire procurement process, from installation and maintenance to system upgrades and retiring old hardware.
Co-Managed IT
Our Co-Managed IT services enhance your in-house IT team with additional support and expertise. We offer network management, cybersecurity, backup solutions, and more, ensuring responsive and efficient IT support while allowing your internal team to focus on strategic initiatives.
Our Mobile Device Management services offer comprehensive control over your organization’s mobile devices. We ensure secure configuration, monitoring, and management of devices, safeguarding your company.
As a Microsoft Gold Partner, our Microsoft services provide comprehensive solutions to maximize your productivity & collaboration. We offer support for Microsoft 365, Azure, and other Microsoft technologies, including setup, migration, management, and more.

Apple Technology
Apple Technology
Companies that have invested in Apple technology for their workforce expect top-tier service and support. At Verity IT, we specialize in Apple technology services, offering comprehensive support from help desk assistance to deployment, management, monitoring, and cybersecurity. We ensure your Apple environment—including iOS, iPadOS, macOS, and tvOS—operates at peak performance.
Our Cloud Services provide flexible, scalable solutions to enhance your business’s efficiency and agility. We offer comprehensive cloud management, including migration, deployment, and ongoing support for public, private, and hybrid cloud environments. Whether you’re looking to move to the cloud, optimize your existing setup, or ensure robust security and compliance, our expert team is here to help.
Account Management
Account Management
Our Account Management service offers personalized, proactive support to ensure your IT needs are consistently met. From regular check-ins and strategic planning to coordinating services and resources, our Account Management team is committed to delivering exceptional service and fostering a strong, long-term partnership.
Need IT Support that Actually Helps?
We’re here to make your life easier.